Username List Cracking
UNIQPASS is a large password list for use. Removed from all passwords: 9. JtR wordlist cracking mode against a list of 551,638 MD5 hashes using. Most of the password cracking tools try to login with every possible combination of words. You can specify the username list along with the password list. Dec 01, 2012 list of windows password cracking software. The program will automatically list all Domain user accounts. Select a user account and click the.
Failed to load latest commit information. The Passwords directory will hold a number of password lists that can be used by multiple tools when attempting to guess credentials for a given targetted service. This will include a number of very popular lists in cooperation with their maintainers, including the RockYou lists maintained by Rob Bowes. Password lists containing the count are located in the 'withcount' folder. Lists over 100Mb have been compressed. Merged.txt.tar.gz contains a merged list of all password lists in the 'Password' directory; it has been sorted and uniq'd.
When it comes to cracking passwords there are only a handful of different attacks that can be leveraged. But when the criteria for these attacks are met they are highly effective. What I will cover in this post is a dictionary attack. But before we begin the attack, it is important to understand passwords and how they are encrypted before we break them. E ncryption Websites and programs do no store your passwords as plain text (.at least they are not suppose to.).
Zoom gfx 8 software. So if your password is Ilovepancakes123!, in the database it will be saved as something like this: 83ddab15adcc129b4b56d2650bf54039. This is the hashed version (MD5) of your password, which is encrypted using a certain algorithm.
There are many different algorithms that programs use. Some are more secure than others. This prevents other people, besides the owner of the account, to be able to see what the actual password is.
If you want to see what your password looks like hashed using a certain algorithm you can use this python program. Import hashlib passwd=rawinput('Enter password: ';) while True: try: hasher=rawinput('Enter the desired encryption method(examples:MD4,MD5,SHA1,FIPS.): ') hashlib.new(hasher, passwd.encode('utf-16le')).hexdigest break except ValueError: print 'The method you entered is invalid' print hashlib.new(hasher, passwd.encode('utf-16le')).hexdigest Sample output: Cracking Now the fun part! So how can we break into someones account? Because many people use very common or predictable passwords we can exploit that. A dictionary attack is using a preset or custom giant list of passwords that we can run against an account. This attack would be non existent if people would set more complex passwords but as attackers we can always rely on human laziness.
Username List
The tool that we will use to crack passwords is hashcat and we will create a custom wordlist. Step 1: Create the custom wordlist A common/basic CTF problem that shows up is the following: Our officers have obtained password dumps storing hacker passwords. It appears that they are based off of Law and Order: SVU episodes and end in 2 digits. 6475c851b56004eb96ab1404252c3a34.
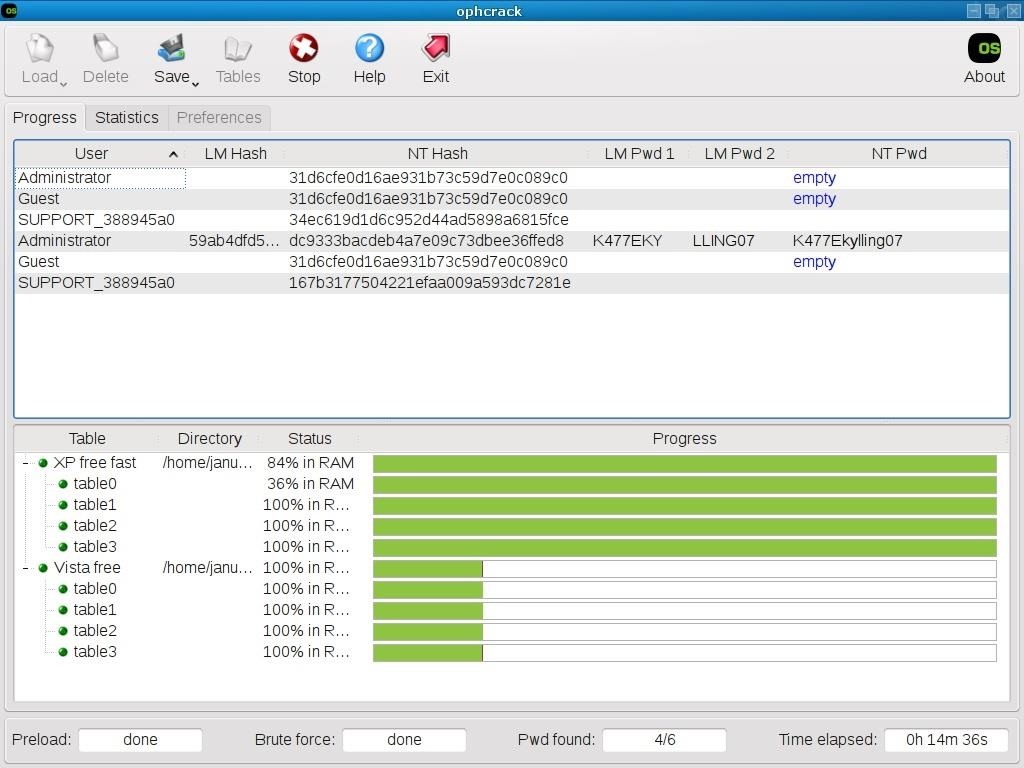
abe6591e06aafc3cf1b0783b120f685e. 969f2ca0a553a137c845ff9b0ad01c96. 8beaaddc4a92a5c52e518ee30ab84d90. 08038f679de74982bfb9bac43d46271a The first step I took was creating a list of episode titles. This was the part that took the most time because I could not find a list, without the extra information,that I could just copy and paste into a text document.The closest I got to a list looked liked this: So I ran this simple python script to delete all the unnecessary information: f = open(/SVU.txt) lines=f.readlines for line in lines: line=line39: Now I have this: But if we look at the prompt it says that the passwords ended in 2 digits. So we know that for each episode there will be 100 different combinations trailing the name (00-99). For example 'Payback18' or 'Payback89'.
So we need to append all those different combinations to the ends of each episode. So I created this script: lines = line.rstrip(' n') for line in open('SVU2.txt') print lines num= len(lines) for names in lines: for x in range(100): print names.lower+x After we output the code from the above to text document we get: Now we have our wordlist! Step 2: Hashcat Now that we have our wordlist we are ready to try to see if hashcat can crack the passwords using it. What hashcat does is it hashes your wordlist using the desired encryption and then compares that to the target hashes. First lets see the options we have in hashcat using the command: hashcat -help The two options we will use are -m and -a. The option -m lets you set the type of hash you want to try to use. For this example we will use MD5 but if you are unsure which you should use try using a online checker like:. The options hashcat gives us are: For -a this is the attack mode the options are (we will be using the straight attack): Now that we know what hash type and attack mode we have, we are ready to run hashcat.
Default Router Password And Username List
Good Usernames List
The command that will we use is: hashcat -m 0 -a 0 'location of hashed passwords list' 'location of custom wordlist' For me this was: hashcat -m 0 -a 0 SVUhash.txt SVU3.txt Output: And we are done! As you can see we got all 5 of the passwords cracked using our custom wordlist.